ssh
Table of Contents
- 1. ssh
- 1.1. https://github.com/moul/awesome-ssh
- 1.2. links
- 1.3. Generar claves ssh en servidor y cliente
- 1.4. scp
- 1.5. ~/.ssh/config
- 1.6. Conectarse por túnel ssh
- 1.7. Estándares de seguridad ssh
- 1.8. SSHd securization
- 1.9. ssh-agent
- 1.10. Mosh: the mobile shell
- 1.11. crontab con otro editor distinto
- 1.12. Proxy jump ssh
- 1.13. Conexión lenta ssh
- 1.14. Tunnelmole, an ngrok alternative (open source) - SES
1. ssh
1.2. links
1.3. Generar claves ssh en servidor y cliente
julian $ ssh-keygen -t ed25519 -b 4096 -o -a 1000 -C "julian" -f rpi julian $ ssh-copy-id -i ~/.ssh/rpi.pub pi@raspberrypi julian $ chmod 600 ~/.ssh/rpi.pub
1.4. scp
1.4.1. https://superuser.com/questions/395356/scp-doesnt-work-but-ssh-does
One possible cause of this type of behavior is having any message print out during the login process on server. Scp depends on ssh to provide a totally transparent encrypted tunnel between the client and the server.
1.5. ~/.ssh/config
Host [vps]
HostName [host]
user [user]
IdentityFile ~/.ssh/[file]
ProxyCommand nc -X 5 -x 127.0.0.1:9050 %h %p # use TOR
Compression yes
ConnectTimeout 300
- Then
ssh-copy-id -i .ssh/[file] [vps]
1.6. Conectarse por túnel ssh
ssh -L 54321:127.0.0.1:5432 -N <ip_externa>- https://unix.stackexchange.com/questions/46235/how-does-reverse-ssh-tunneling-work/118650#118650
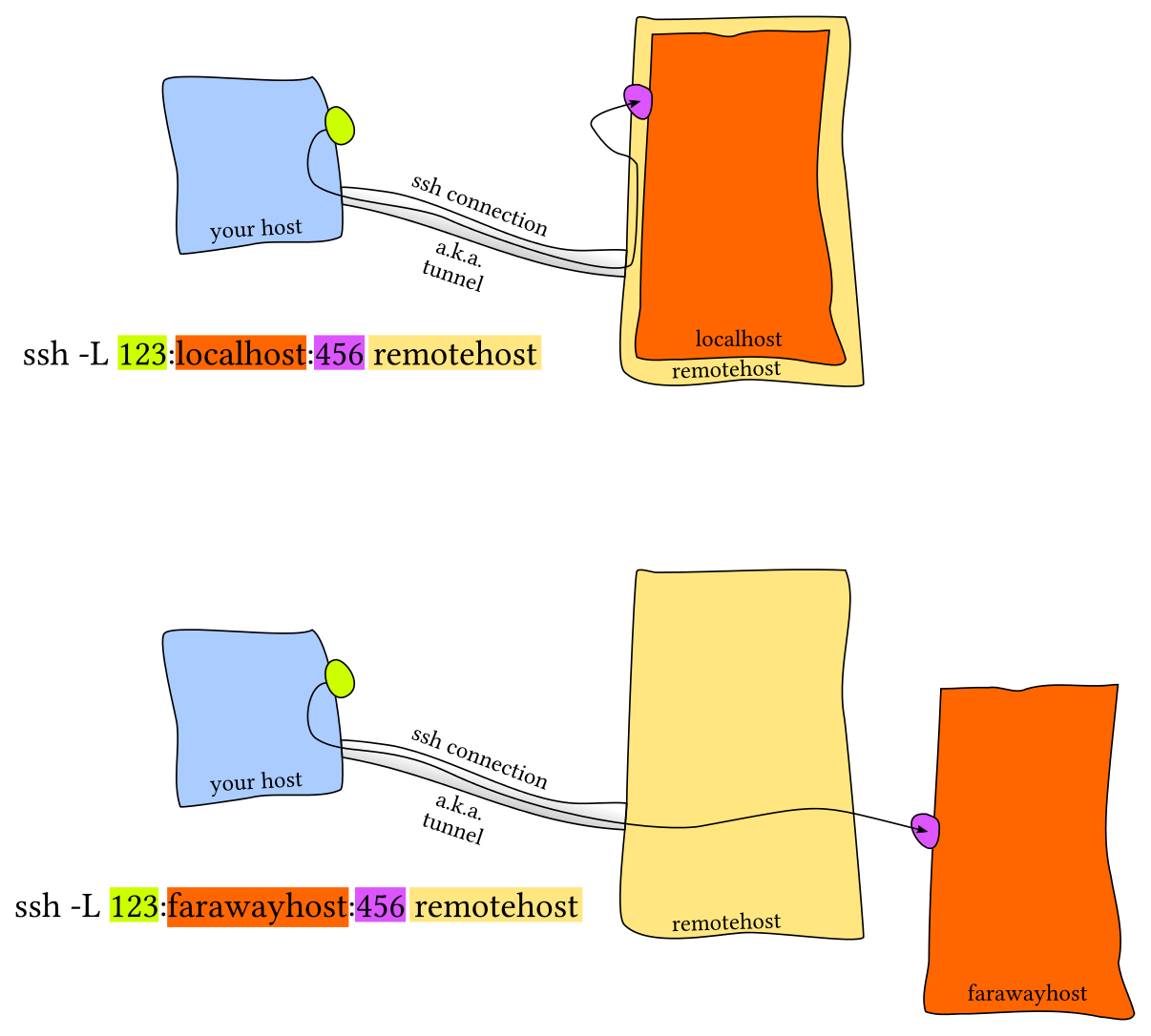
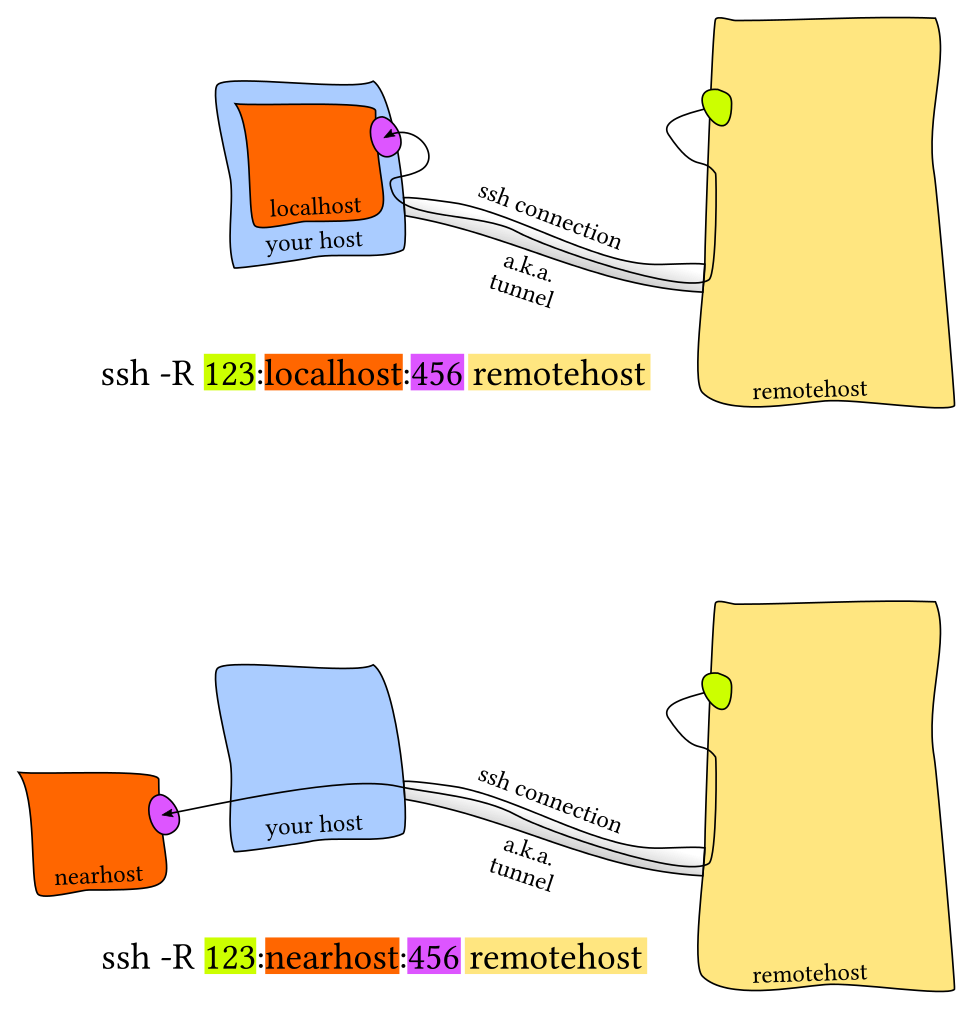
1.7. Estándares de seguridad ssh
1.7.1. Keylength - Cryptographic Key Length Recommendation
1.8. SSHd securization
Cool, now we are on the server. First thing to do is to disable password
login via SSH.
/etc/ssh/sshd_config find #PasswordAuthentication yes and change it
for PasswordAuthentication no
Then, let’s create a new user (in case you are loging in as root).
useradd -G sudo -s /bin/bash -m [user] passwd [user]
In order to be able to log in directly with this user via ssh, we should
copy our public key to its own ~/.ssh/authorized_keys file. We can
copy the one from the root user and change its permissions.
mkdir /home/[user]/.ssh cp /root/.ssh/authorized_keys /home/[user]/.ssh/ chown -R [user]: /home/[user]/.ssh # [user]: will make [user] the owner and : will make [user]'s default group the folder's owner group user:user in stead of user:root (group not changed)
Now you should try loging in with this user (modify local
~/.ssh/config if necessary). If all goes right, you can now disable
SSH root login.
/etc/ssh/sshd_config find PermitRootLogin yes and change it to
PermitRootLogin no
For now on, you shold connect via ssh with a regular user using keypairs
in stead of plain text passwords, and then login as root with
sudo su -. This adds a layer of protection against 0-days, bots,
script kiddies… ;-)
Bonus: you should definetly take a look at
fwknop.
Bonus 2: /etc/passwd -> /usr/sbin/nologin
1.9. ssh-agent
https://superuser.com/questions/988185/how-to-avoid-being-asked-enter-passphrase-for-key-when-im-doing-ssh-operatio
Start ssh-agent if not started:
eval `ssh-agent -s`
Add your private key using ssh-add
ssh-add ~/.ssh/id_rsa_key Enter passphrase for /home/user/.ssh/id_rsa_key: Identity added: /home/user/.ssh/id_rsa_key (/home/user/.ssh/id_rsa_key)
Check if the key is added (parameter is a lowercase L):
ssh-add -l 2048 55:96:1a:b1:31:f6:f0:6f:d8:a7:49:1a:e5:4c:94:6f /home/user/.ssh/id_rsa_key (RSA)
Try to connect to your Git server:
ssh git.example.com
1.10. Mosh: the mobile shell
mosh the mosh
1.11. crontab con otro editor distinto
Útil si tienes más usuarios que usan sudo y no usan vim
sudo sh -c "export EDITOR=vim && crontab -e"
1.12. Proxy jump ssh
“Proxyjump, the SSH option you probably never heard of” por Khris Tolbert https://medium.com/maverislabs/proxyjump-the-ssh-option-you-probably-never-heard-of-2d7e41d43464
1.13. Conexión lenta ssh
- ssh connection takes forever to initiate, stuck at “pledge: network” - Server Fault
A comprehensive guide to fixing slow SSH logins – JRS Systems: the blog
En la RPi4 era comentar esto en/etc/pam.d/common-session:
#session optional pam_systemd.so